Malware Raises Security Risks in Supply Chain

Security experts are increasingly worried about the security of the supply chain with reports of more than 20 incidents where rogue retailers have managed to pre-install malware on new Android phones.
Bought a brand-new (Android) phone recently?
It could still have malware.
As reported by Robert Lemos of eWeek, rogue retailers are unpacking phones made in China, installing malware and then selling the infected phones on the open market, security firm G DATA stated in a report released yesterday.
The scheme involves infecting mainly local brands of Android phones - such as Alps, Xiaomi and even a line of devices known as “NoName” - but also it affects phones from well-known international brands such as Huawei and Lenovo.
While some compromised phones have been discovered as far away as Europe, the devices were mainly sold through Chinese retailers, likely street vendors in urban areas of China, according to G DATA’s report.
The incidents, which involve nearly two dozen brands of phones, underscore the current difficulties in securing technology as it moves through the supply chain to its destination.
“This happens before the user ever gets the phone,” Andy Hayter, security evangelist with G DATA, told eWeek. “We checked with some of the manufacturers and they are telling us that it is not happening on their end of the supply chain.”
The incidents underscore the dangers of untrusted supply chains. Companies and government agencies have grown worried about the security of the supply chain - the flow of goods from manufacturer to retailer to consumers.
G DATA Releases Mobile Malware Report for the Second Quarter of 2015
Security Researchers Discover Pre-Installed Spyware Embedded in Smartphones Shipping from Asia
Over 190.3 million people in the U.S. own smartphones, but many do not know exactly what a mobile device can disclose to third parties about its owner. Following their findings in 2014 that the Star N9500 smartphone was embedded with extensive espionage functions, G DATA security experts have continued the investigation and found that over 26 models from some well-known manufacturers have pre-installed spyware in the firmware.
However, unlike the Star devices, the researchers suspect middlemen to be behind this, modifying the device software to steal user data and inject their own advertising to earn money.
G DATA have released their Q2 2015 Mobile Malware Report, which discusses these findings as well as analyzes mobile malware samples found over the past quarter.
“An estimated 2.5 billion people worldwide use a smartphone or tablet to go online. Chatting, surfing and shopping are possible anytime, anywhere thanks to smartphones and tablets. At the same time, the number of mobile malware apps has sharply increased in the past three years,” says Christian Geschkat, G DATA Mobile Solutions Product Manager. “Over the past year we have seen a significant increase in devices that are equipped with firmware-level spyware and malware out of the box which can take a wide range of unwanted and unknown actions including accessing the Internet, read and send text messages, install apps, access contact lists, obtain location data and more - all which can do detrimental damage.”
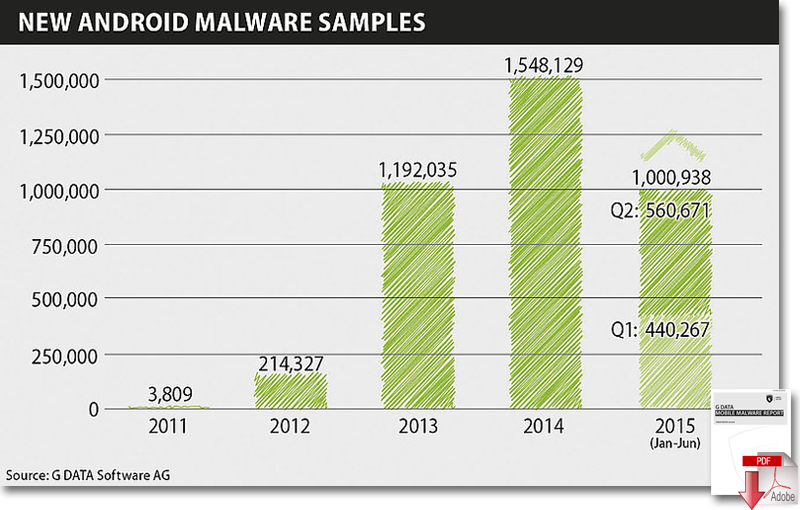
New Record: over a million new Android malware strains in six months
During the second quarter of 2015, the experts analysed 6,100 new malware samples every day. By comparison, in the first quarter of 2015, they saw about 4,900 malware apps per day, representing an increase of almost 25 percent quarter over quarter.
Additionally, the first six months of 2015 has already broken all previous malware records – over a million new Android malware strains (1,000,938) were discovered within just six months. In those six months, the analysts have already discovered almost as many Android malware instances as in the whole of 2013.
G DATA estimates that there will be over two million new malware apps by the end of the year.
Further forecasts
- Year of records: In the second half of 2015, G DATA security experts expect yet another significant increase in Android malware instances. A figure of over 2 million new Android malware strains for the year is likely, which would set a new record.
- Android malware is becoming more refined: Hacking Team, an IT company that develops a wide range of malware for intelligence services and governments, suffered a cyber attack this year. After this attack, corporate data and source code for an Android malware strain were published. G DATA security experts expect cyber criminals to exploit this easily accessible knowledge base and publish large numbers of more mature Android malware.
Related: Supply Chain IT Risk Mitigation Still Work in Progress

Article Topics
G DATA News & Resources
Mobile Malware Report for Q1 2015 Malware Raises Security Risks in Supply ChainLatest in Technology
U.S. Manufacturing is Growing but Employment Not Keeping Pace The Two Most Important Factors in Last-Mile Delivery Spotlight Startup: Cart.com is Reimagining Logistics Walmart and Swisslog Expand Partnership with New Texas Facility Taking Stock of Today’s Robotics Market and What the Future Holds Biden Gives Samsung $6.4 Billion For Texas Semiconductor Plants Apple Overtaken as World’s Largest Phone Seller More Technology