The Supply Chain Silent Threat – Cyber Attack
High-value cyberspace attacks can change the status quo. Whether they involve stealing the blueprints for a new aircraft design or disrupting the supply of electrical power, all of them have one weakness in common – the supply chain.
At the height of the Cold War, in June 1982, a US surveillance satellite spotted a substantial explosion in Siberia. A brief inquiry revealed that the source of the explosion picked up by the satellite was the new trans-Siberian gas pipeline the Soviets had laid in that region.
A short while prior to that event, the KGB, the USSR’s Committee for State Security, had completed a sophisticated operation that seemed audacious even by the standards of the James Bond novels.
The objective of that operation was to place a spy in a Canadian software company so as to obtain a management software system for the new gas pipeline.
Line-X Department
The spy in question was not aware of the fact that the software he stole had been ‘modified’ by specialists of the CIA, the Central Intelligence Agency of the USA, who had inserted a few additional lines of code into the original software. The spy went back to the USSR with the software that was subsequently installed in the management systems of the new pipeline, and a short while later, that software led to the explosion that was picked up by the US satellite.
Thomas Reed, a senior official of USAFintelligence at the time, later described the result of the CIA operation as “the most monumental non-nuclear explosion and fire ever seen from space”. All of this was achieved without using even a single missile or a bomb – only by a few lines of program code.
This espionage operation came to be known as Operation Line-X, for the KGB department charged with stealing technological secrets from the USA in the 1970s and 1980s. In its heyday, the Line-X department employed about 200 agents working under 10 different KGB stations in Western countries. They stole everything: metal parts, software, blueprints and thousands of documents that contained information about radar systems, computer systems, machinery and semiconductors.
That department was unveiled by Vladimir Vetrov, a Soviet double agent run by the French under the codename Farewell. The French shared the information he had provided with the CIA, and that led the Central Intelligence Agency to the realization that they could fool the Russians by inserting “modified” hardware and software components into the systems the Russians were stealing.
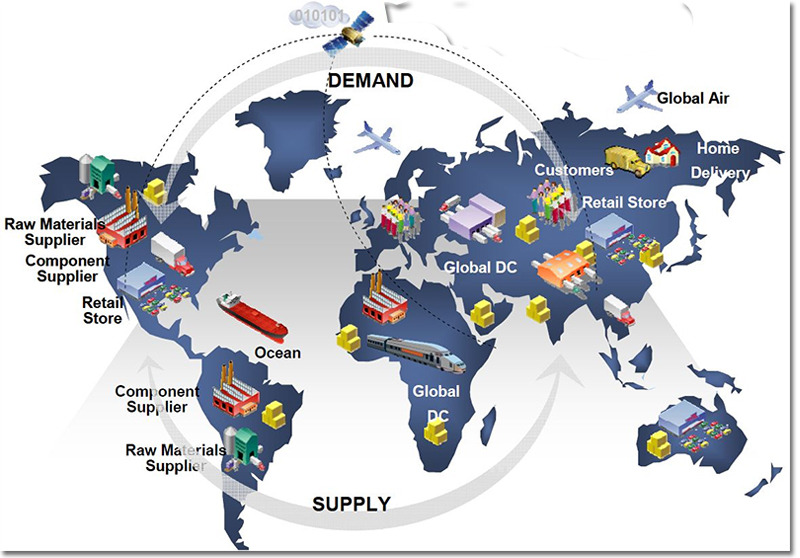
International Visibility through Satellites and Cloud Technology
Silent Threat
An OECD report from 2013 found that today, more than half of the products manufactured worldwide are “intermediate (semi-finished) products” – products used for the manufacture of other products, and more than 70% of all services are intermediate services.
The fragmentation of the production chain is the strength of many corporations around the world. It is the result of technological progress, the desire to minimize manufacturing costs, the globalization of resources and markets and reforms in commerce and exports in many countries. Equally importantly, this trend follows the principle of relative advantage.
The supply chain is a range of resources and processes associated with the suppliers, purchasers and contractors involved in the process of developing, manufacturing, handling and shipping products and services to the various buyers. Damaging the finished system through the supply chain is possible at any point along its life cycle, and protection becomes much more complex.
Supply chains possess characteristics that make them very difficult to protect and provide the attacker with an advantage: they are complex, they are dispersed around the globe, they are interconnected, long and made up of numerous logic links, their routes are not regular and there are different layers of outsourcing. The implication, as far as the defender is concerned, is a difficulty in understanding the elements used by each system and each subsystem, jointly and individually.
As far as the organization is concerned, it is a hefty problem that may be manifested through two threat categories. The first category is degraded functionality. Hardware and software quality is difficult to test and there is always concern about counterfeit components that do not conform to the required standards. Problems and malfunctions are encountered even when a supervisory mechanism is in place.
Infected IP Addresses (24 hour period, June 29th 2010)
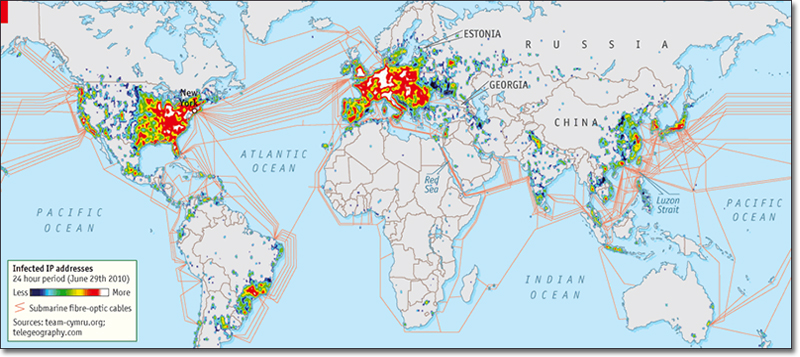
For example, the US Government Accountability Office (GAO) found, in 2011, that the US military had acquired thousands of counterfeit electronic components from an American contractor. According to the US GAO, a number of operational systems suffered from significant operational delays as a result. Among those systems was a state-of-the-art, ultra-high frequency military satellite, the next generation (Block IIF) of the GPS systems, a satellite that is a part of the SBIRS system and other systems.
The second threat category is undesirable functionality. In this case, a malicious code is inserted into hardware or software elements during the manufacturing process, to be utilized when the “modified” hardware or software elements have reached their final destination. Another threat involves poorly-developed software whose weaknesses can be exploited. Owing to the complexity involved in analyzing the supply chain, the spotting (or exploitation) of weaknesses in the supply chain can take many years.
The Danger: Total Collapse of the USA within 15 Minutes
Although the trans-Siberian pipeline event took place more than 30 years ago, it still denotes the beginning of the category of attacks known as attacks against the supply chain. In the professional jargon, some people refer to these attacks as using logic bombs – a comparison intended to assign to these attacks the same severity assigned to attacks using kinetic weapons.
Since the trans-Siberian pipeline event, quite a few attacks of this type have been staged with the purpose of hitting the weaker links in the supply chain of a technological product being delivered to the enemy. In the global labor market, different components of the same product may be manufactured in several different countries and assembled at different focal points – a fact that increases the number of weaknesses in the supply chain makes these attacks particularly desirable.
Such attacks are being staged even as these lines are being written. One recent attack was the Icefog attack identified last September by Kaspersky Lab and aimed mainly against corporations and organizations in South Korea and Japan – global industrial centers.
Another attack was revealed through the documents disclosed by Edward Snowden, the whistleblower who used to work for NSA. Snowden’s documents revealed that a special cyber unit of the NSA, named TAO, had planted electronic components and a malicious code in products on their way to an end user.
Nyxem.E (Blackworm Virus) Global View
According to foreign sources, the insertion of the Stuxnet virus into the command and control center of the Iranian uranium enrichment facility in Natanz had been accomplished by attacking several points along the supply chain. According to those sources, the virus was probably inserted by a technician who came to the facility for some maintenance work. The designers of the Stuxnet virus demonstrated that even if a computer is not linked to a network, it is connected to a supply chain and can be attacked from that direction.
A recent report claimed that China had attacked and stolen all of the plans of the Australian Secret Service HQ. Another incident reported just recently revealed that modified hardware components were inserted into two spy satellites France intends to sell to the United Arab Emirates in the coming years.
The threat of attacks against the supply chain has not skipped Israel, and senior executives in the Israeli defense industries have voiced, in utmost discretion, their apprehension of counterfeit electronic components. Last year, such components were spotted in US-made aircraft, and the possibility that such components have found their way into Israeli products cannot be ruled out. It should be noted that these components constitute “a silent threat”, namely – they appear to be passive, and only when specific conditions, such as a specific temperature, a specific speed or a specific location have been met – they come to life and damage the system in which they are installed.
Richard A. Clarke, a former White House employee and special advisor to the president on cyber security, envisioned in his book a catastrophic collapse of the USA in just 15 minutes owing to damage inflicted on the supply chain required in order to maintain critical infrastructure and utility systems.
Computer system bugs will paralyze military electronic mail systems; refineries and pipelines will explode; air-conditioning and traffic light control systems will collapse; freight train and underground transportation systems will be disrupted; the data of the financial system will be scrambled; the electrical power network of the Eastern USA will be paralyzed and control over satellites orbiting planet Earth will be lost.
According to this doomsday scenario, American society will disintegrate, food and money will run out, and the worst of all – the identity of the attacker may remain a mystery.
About the Authors
Ram Levi is the founder and CEO of the Konfidas Company and a senior research fellow at the Yuval Ne’eman Workshop for Science, Technology & Security at the Tel-Aviv University.
Ami Rojkes-Dombe is the technological correspondent.
Source: Israel Defense













