Malware Hidden In Chinese Inventory Scanners Targeting Logistics and Shipping Companies
TrapX discovers ‘Zombie Zero’ advanced persistent malware - Made in China; state sponsored attack targeting shipping and logistics industry worldwide.
TrapX, provider of the fastest growing sensor-based HoneyGrid™ in the world, announced the discovery of a highly sophisticated, polymorphic advanced persistent malware dubbed “Zombie Zero” targeting the shipping and logistics industry across the globe.
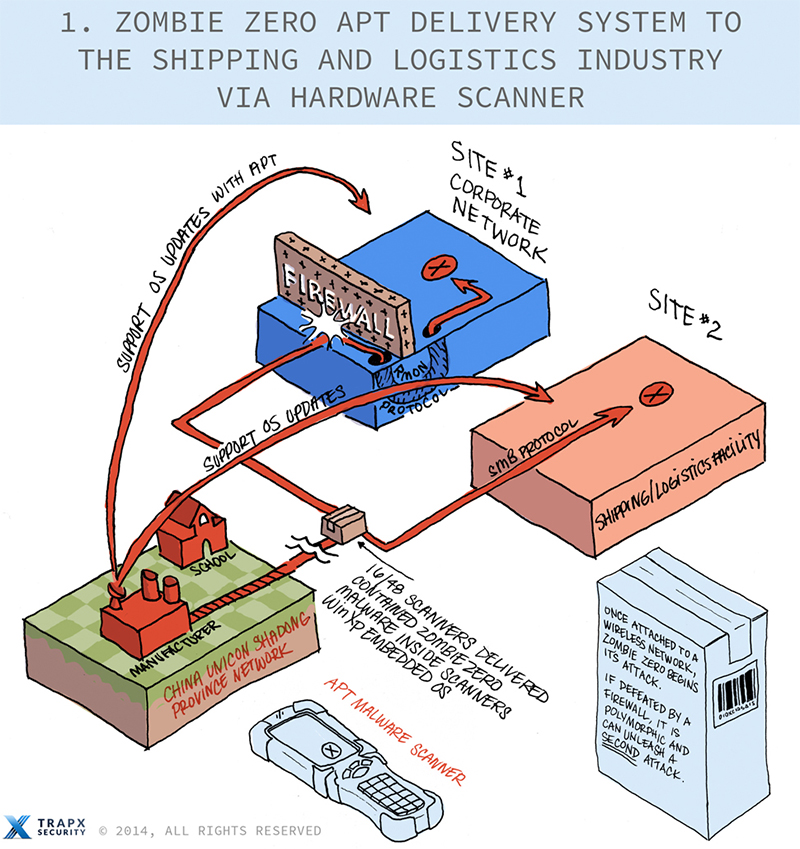
Weaponized malware was delivered into shipping and logistics enterprise environments from a Chinese manufacturer responsible for selling proprietary hardware for terminal scanners used to inventory items being shipped or transported in and out many countries.
The malware was delivered through the Windows embedded XP operating system installed on the hardware at the manufacturer’s location in China and could also be downloaded from the Chinese manufacturer’s support website.
A variant of this malware was also sold and delivered with the same hardware product to a large manufacturing company as well as to seven other identified customers of this hardware product worldwide.
Source: TrapX Zombie Zero report
Description of Zombie Zero Behavior and Attack
- Once the scanner was attached to the wireless network and put into production it immediately began an automated attack of the corporate environment using the server message block protocol.
- The shipping and logistics target installed security certificates on its scanner devices for network authentication but because the devices were already infected with the advanced persistent malware from the manufacturer, the certificates were completely compromised.
- The scanned data (origin, destination, contents, value, to, from, etc.) was copied and sent out to an established comprehensive command and control connection (CnC) to a Chinese botnet that was terminated at the Lanxiang Vocational School located in the “China Unicom Shandong province network”. The Lanxiang Vocational School has been linked to on-line attacks of Google and implicated in the Operation AURORA attack. The Chinese scanner manufacturer is located blocks away from the Lanxiang Vocational School.
- A second payload was then downloaded from the botnet that established a more sophisticated CnC of the company’s finance servers giving the cybercriminal access to corporate financial data, customer data, detailed shipping and manifest information.
- The exfiltration of all financial data as well as CRM data was achieved providing the attacker complete situational awareness and visibility into the shipping and logistics targets worldwide operations.
“The problem with legacy security technologies is that they are not able to adapt to defend against emerging threats in real-time,” said David Monahan, Research Director at Enterprise Management Associates. “Today’s threat actors are smarter than ever morphing their attacks multiple times to achieve the goal of undermining existing security defenses. The next generation of security solutions must be just as adaptable to counter these modern threats.”
“Security futurists have long favored honeypots as a way to actively defend the network. The challenge with honeypots is that they’ve largely required manual deployment. They’ve been difficult to scale across the network, particularly in rapid response to current attacks,” said Yaniv Alfi, cofounder and CEO. “TrapX has taken the honeypot idea to the next level. We provide a virtualized honeygrid platform that not only emulates hundreds of services across the network—our software also senses hostile scans and spins up targeted honeypots where they’re needed most in order to identify cybercriminal, insider, or nation-state activity.”
TrapX, formally known as CyberSense, conducts powerful real-time analytics and threat intelligence to support Adaptive Defense of the network while providing full incident lifecycle management – detection, remediation and prosecution. The TrapX 360 platform is designed to detect and interdict lateral movement within networks and keep attackers from establishing footholds in the network nerve center.
The Anatomy of the Attack
The move to cloud based technologies and virtualization has amplified the rate of change within data centers. Operations teams stand up services one day, and spin them down another. Capabilities come, and capabilities go. And throughout the flux, the number of virtual machines and services continues to grow, week after week, month after month.
Corporations have fought to keep pace with threats to these fluid data center environments. But in today’s world, the threats evolve just as quickly as your business. This coupled with an uneven security playing field full of nation states and crime syndicates who possess significant monetary resources and capabilities. The active defense of your company assets is now directly tied to your ability to detect, analyze, and interdict Zero-Day threats from a world of bad actors.
Attacks keep slipping through corporate defense in depth architectures because legacy security products aren’t built to adapt to threats in real-time. Today’s threats are fluid like today’s clouds and data centers. The next generation of security technologies must be just as elastic to counter these modern threats.
This is where TrapX changes not just the security model but also the business model. We change the asymmetric aspect of the cyber battlefield by giving the net defenders the automated tools to defeat the attacking perpetrators creating an elastic and Adaptable Defense™.
In support of our existing customers and educating corporate and government entities, TrapX will continue to publish on a monthly basis The Anatomy of the Attack. With the largest sensor based HoneyGrid™ in the world, the TrapX 360 platform is uniquely positioned to detect, analyze, and report in real-time Zero-Day and APT threats in a completely automated framework.
Subscribe to the monthly The Anatomy of the Attack newsletter
TrapX today also released a free tool for forensics investigators called Threat Inspector. “We’ve cobbled together some top open source tools and put in a front-end wizard that will allow any engineer to get forensics reports off infected machines,” TrapX says.
About TrapX
TrapX has invented a purpose-built, virtual appliance-based security platform that provides real-time threat protection to enterprises and governments worldwide against the next generation of cyber attacks. The TrapX360™ Platform provides real-time, adaptive threat protection by leveraging our patented HoneyGrid™ malware trap and DPI technology. TrapX360™ traps zero-day malware in its virtualized sensor network or HoneyGrid™ and next-generation malware traps before the malware can inflict significant damage to customers’ data centers or cloud deployments. Combined with fully automated advanced forensic capability and a threat intelligence fusion center, TrapX provides the most comprehensive context sensitive alerting and reporting in the market.
Related: Cyber Attacks Targeting Smartphone Supply Chains